Burger King wasn’t lovin’ it this week when their Twitter account was hacked by internet trolls. The @BurgerKing account was hacked around noon yesterday, and promptly tweeted that Burger King had been bought by McDonald’s. The account’s profile picture and page branding had been changed to look like McDonald’s, plus the culprits tweeted unintelligible obscenities and racial epithets. This is what a community manager’s nightmares are made of. But the Twitterverse was having a field day:
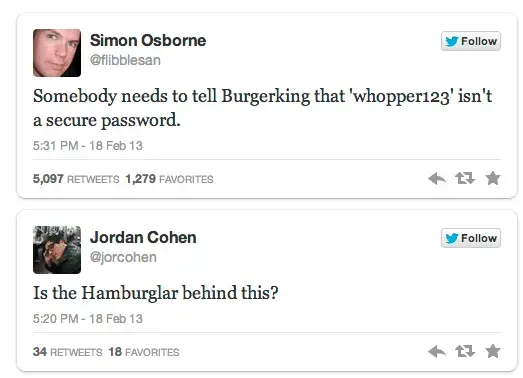
It took a little over an hour after the hack went public for Twitter to take down the account. The morning after, @BurgerKing has been restored to its rightful owners. As a result of the hack, Burger King’s Twitter account gained 10 thousand new followers. (No, this is not a good strategy to gain followers, so don’t even think about it!) So, what does this mean for your brand? What measures can you take to protect your brand?
A workflow for creating secure passwords
When most users are asked to create strong passwords, they choose the following method:
- A root word in their language
- A number to follow it
Most password hackers know this pattern, and “calibrate” their tools accordingly. For me, a strong password is a random password. There are tools out there, like 1Password, that will create random passwords for you. Password management systems also keep track and auto-populate passwords for you, as long as you use an authorized machine.
Some password management systems also allow you to collaborate and share passwords across teams, making this the best workflow for creating truly strong passwords, storing them safely, and sharing them responsibly. No more passwords kept on spreadsheets, please. (Also, Kittens123 is probably not a good password.)
It goes without saying that you should create a different, random password for each account you manage. If you create one random password, however strong it may be, if that gets hacked, then you’re giving your hackers keys to your whole kingdom.
Your brand needs a social collaboration workflow
If your brand has a big enough social presence, chances are you need a team to work on and collaborate on social media accounts. Some folks use the trust method and will share a password with you, and you will need to do what you can to keep that password safe. Other teams (and I have seen this) keep a spreadsheet with passwords and pass it around. In addition to using a password management system as I detail above, your brand should also choose a “collaboration tool.”
A collaboration tool, also known as “social media monitoring” or “brand management” tools, allow you to establish a true team workflow. Tools like HooteSuite or Radian6 allow employees to login to the tool using their own social media credentials, but post to a single Twitter account (like say, @BurgerKing). Allowing your employees to use their own Twitter account as credentials for accessing a social collaboration tool enables you to assign certain content to individual team members, while also making each team member accountable for their engagement. (Here’s an example of what collaborating on Radian6 looks like.)
Dell is a great example of social media team collaboration. (Full disclosure, I used to work at Dell.) Dell uses Radian6 as their social monitoring and engagement tool. Radian6 would take care of setting up tool instances on the backend, and employees would download a ready-to-use instance of Radian6. You would work with Radian6 to get access to the particular team account you needed, but you used your own social accounts to login, manage, and engage. For example, employees working in social media on behalf of Dell were required to set-up their own “your name at Dell” Twitter account. As an employee, you would use this “at Dell” Twitter account to contribute to a specific corporate Twitter account. If you take a look at the @Dell Twitter account, you can see the accounts and initials of the employees contributing to that account on the upper left-hand side. Not only does this approach allow for greater transparency, but it also humanizes your brand by letting your audience see that there are real people behind your account.
Here’s an example of what a workflow for a social media account looks like (from The Financial Brand):
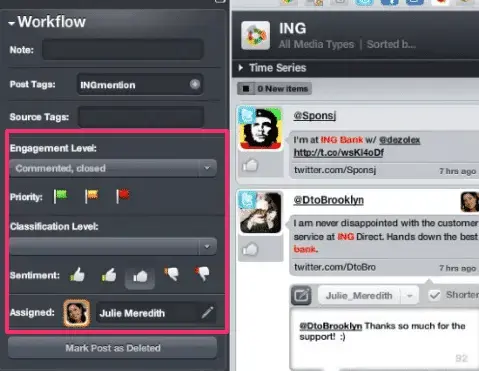
As you can see, a social media mention gets tagged as a comment or action, and you can mark it as positive, negative or neutral, in addition to assigning it to a specific team member.
Not only does a collaboration tool simplify your workflow, but it allows community or social brand managers to share accountability. It is through this shared accountability, trust and transparency that good social media teams are built.
When a staff member goes astray…
Currently, we don’t know how exactly the Burger King Twitter account was hacked. But judging by the fact that Jeep’s Twitter account also got hacked by the same folks, it is safe to assume the culprits are somehow guessing or resetting account passwords.
However, there are situations in which a disgruntled employee has hijacked an employer’s social accounts:
- An HMV employee live tweets layoffs.
- A Marc Jacobs intern hijacks their Twitter account on his last day, calls Jacobs a tyrant.
Meltdowns like these happen to brands that don’t know who has a key to their kingdom. Here are a few tips on avoiding this situation:
1. Always keep track of who has access to your accounts! This process becomes easier once you establish a collaboration tool that can easily allow you to grant and remove access from particular team members. Disable access for employees who may be out on leave or on extended vacation to avoid potential hacks while members are away.
2. Offer training to employees who will be tweeting or posting on behalf of your company. I am amazed at how many companies don’t offer professional training to staff members who will be representing their brand on social media. After all, these positions are very public, and you should set engagement policies and training in place to ensure your brand is represented correctly. Moreover, establishing training for employees handling social media will help your employees know that with great power comes great responsibility — it is a big deal to represent a brand through social. Taking the time to train your employees will let them know you do take this seriously, and as a result, they will feel valued. Often times, employees who go rogue on social media are employees who feel undervalued by the company they represent.
3. Encourage your social media staff to up-keep their own personal social presence. Individuals who work in social often tend to neglect their own presence over maintaining the social media presence of the company they represent. As a result, if things go wrong, or the employee has to leave the company, the individual is left with no leg to stand. Encourage your employees, especially those who handle your social media accounts, to upkeep their own accounts. A company that values their employees’ personal brand and encourages them to grow it, is a company that will foster happy (social) employees. Allowing your employees to upkeep their own accounts also means they will have an online support system when / if they leave your company, resulting in less anxiety on both sides when a departure arises.
3. Who owns a social account? Establish a policy. It is unclear who owns employee Twitter accounts at the moment. The current best practice in the industry is to have branded or unbranded individual accounts. To go with my former Dell example, when I worked at Dell, I had my own @CecyAtDell account, but kept my own personal Twitter account. The policy stated I get to own my personal account, but Dell owns the followers and engagement on my AtDell account. This means when you leave the company, under whatever terms it may be, your employee still has ownership of their own brand, but you as a company still get to own the engagement and relationships you’ve gained.
To wrap things up…
These tips should serve as a good guide to get you started protecting your account, but what will ultimately help you stay on top of your social engagement is to establish guidelines and good policies, plus foster a strong team culture that shares the load and collaborates together. It goes without saying Four Kitchens is always here to help you with our consulting prowess.
Resources:
Creating strong passwords is easier than you think.
XKCD makes an excellent point about how we have been teaching password security wrong.
How Google fights account hijackers.
Making the web a better place to teach, learn, and advocate starts here...
When you subscribe to our newsletter!
